- PIX Command Reference
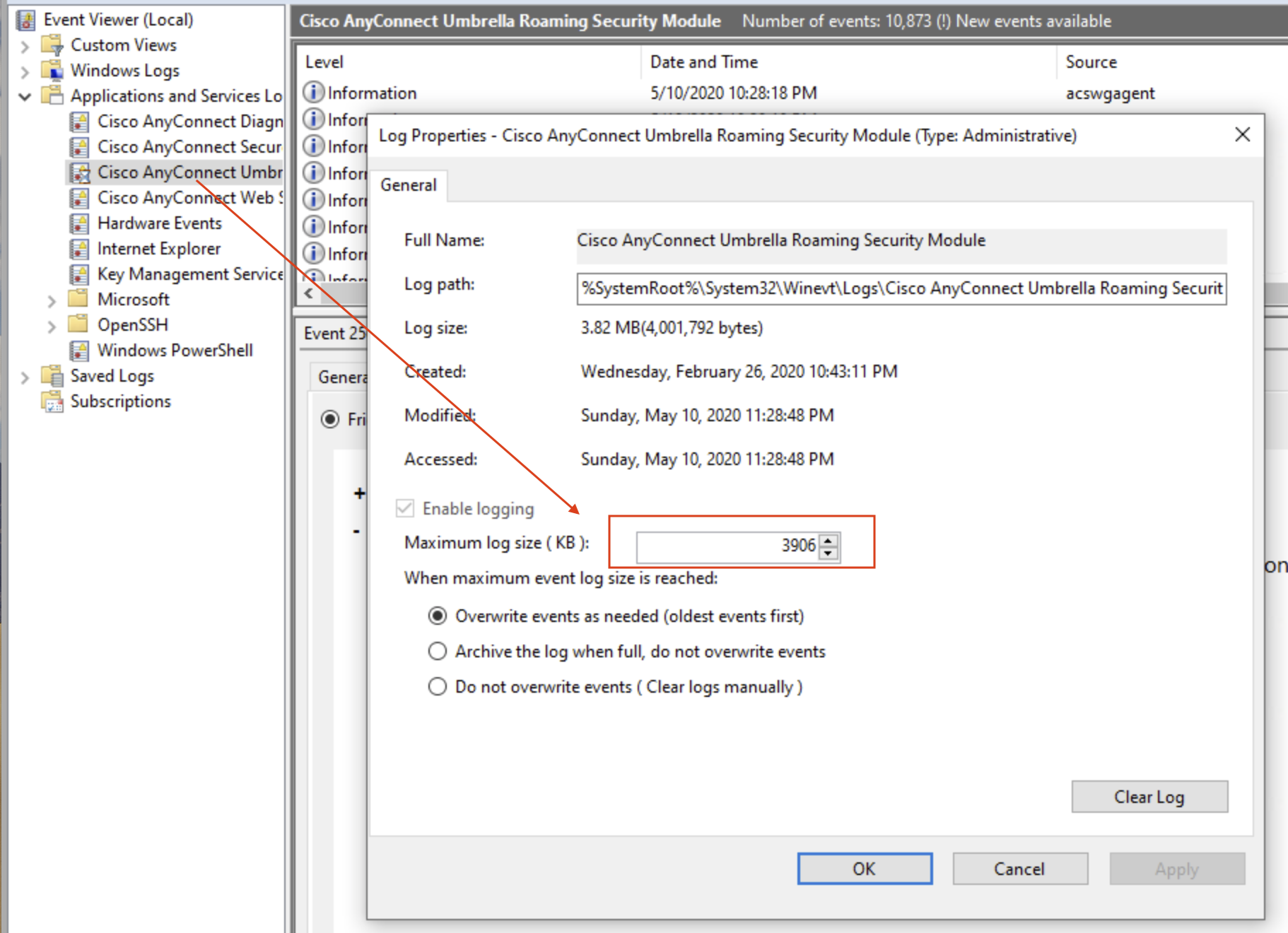
- Troubleshooting And Session Logs For AnyConnect For VPN For ...
- Cisco Anyconnect Client Logs
Cisco Vpn Debug Log, Cisco Clientless Vpn Rdp Plugin, Vpn Umontrealal, Incapable Connecter Nordvpn. Debugging a Cisco SSL VPN connection. We have been using a Cisco 3005 SSL VPN Concentrator for a while now. What attracted was the fact you didn't have to install a client on the machine.
Oct 05, 2017 So the sh crypto debug-condition tells us the conditional debugging is turned on and it’s filtering by the IKE peer IP Address. Now when you start debugging the crypto process you will only see messages that match the peer address of 10.1.1.1, which will certainly make looking through debug logs much easier. Open AnyConnect window and make sure it's in focus. Press this key combination, Left Shift + Left Alt + L. There is no response. Right click on AnyConnect icon in Windows System Tray. Select Extended Logging so it has a check mark displayed. NAM now logs detailed debug messages. Most of the VPN issues you'll want to debug can resolved debugging the IKE portion of the debug. BTW, I'm assuming you mean debugging while SSH'd into the ASA itself.Depending on your code version. Debug crypto ikev1 1-254 (start with 127, then 254) debug crypto ikev2 1-254 (start with 127, then 254).
As wireless networks have evolved in the past years it is getting harder and harder to troubleshoot advanced environments where there are a lot of different key players involved: you got the APs and their WLC, the AAA-servers and the clients themselves to keep track of and try to sort out what is going on during times of trouble.
PIX Command Reference
Cisco WLCs has a lot of useful debugging commands that can be run in CLI but trying to fully understand what is going on can be hard at times. Way too many debugging events are poorly “explained” as they fly by the command line and I often find myself having to look up weird messages and status codes afterwards.
Cisco themselves, being aware of this issue, has a tool published on their website called Wireless Debug Analyzer. It is listed as a tool used by the Cisco TAC to quickly parse through debug logs/output and making them more readable to the user. The idea is that you save the debugging log of a misbehaving wireless clientto a text file and then upload that text file to the tool’s website where it will be processed and “translated” into (hopefully) something better.
You can find the tool at https://cway.cisco.com/tools/WirelessDebugAnalyzer/ (Cisco login required)
According to the very short documentation, all you need to upload is a text file containing the debug ouput of the command debug client <mac-address>. There is also a short footnote about the tool also being able to read some of the debug output from the “debug aaa/mdns/webauth…” commands.
Parsing a successful 802.1X login (debug client <mac> only)
The first test was done using a debug client <mac-address> of a smartphone successfully connecting to an 802.1X SSID using PEAP-MSCHAPv2 and authentication method. The original debug output was around 400 rows of ouput and after putting it through the parser we ended up with this:
Troubleshooting And Session Logs For AnyConnect For VPN For ...
I’ve highlighted some of the intreresting messages where we can see that EAP-authentication takes place and is successful based on that the RADIUS server (ISE in this case) permits the access. What I would’ve loved to see here is what kind of access is given (VLAN assignment, ACL assigment or similar) but with this particular debug it’s as good as it’s gonna get using this tools, even if the original debug output tells us what kind of AAA Override took place (in my case I assigned a particular VLAN to the client).
Parsing a successful 802.1X login (debug client <mac> and aaa)
By adding debug aaa packets to the mix in addition to the debug client <mac-address> command, we do get a lot more debug output which gets translated by the tool when we upload the debug output text file.
This time we get to see which AAA-server (RADIUS) IP-address was used to authenticate this client device. For some reason, as you can see, a lot of RADIUS sessions were created during the authentication of this client device (Radius requests/challenges) but ultimately the authentication was successful and an Access-Accept packet was sent to the WLC. However, still no word on other attributes that could’ve been sent to the WLC such as VLAN assignment or ACL assignment.
Cisco Anyconnect Client Logs
Parsing a failed 802.1X login (debug client <mac>)
Once again we are only running the debug client <mac-address> command but this time I will deliberatly fail the 802.1x authentication by typing in the wrong password.
The information translated for us from this log is pretty weak, as you can see there isn’t much being said about the authentication at all and at the end of it we are not even being told the authentication failed, only that it WLC/AP asks the device again to identity itself.

Parsing a failed 802.1X login (debug client <mac> and aaa)
By adding debug aaa packets to the mix in addition to the debug client <mac-address> command, we do get a some more debug output but most of it is just repeat text telling us the WLC is resending the authentication to the AAA-server over and over again in new RADIUS sessions.
Verdict
The Cisco Wireless Debug Analyzer isn’t as great as it could’ve been, I love the idea of this tool making troubleshooting simpler but it doesn’t seem advanced enough. If anything, it is useful at dividing the debug output into sections even if the “translated” result is not very well-described or not there at all. With the newer WLCs actually running Ciso’s own IOS-XE software instead of AireOS which has been used for the past 10 years or so, I don’t see Cisco putting any more effort into making this tool better, but I guess we have to keep in mind this tool was made by a couple of engineers at Cisco so maybe it can’t be considered a “real” product where users can demand new features. The tool is not very useful for troubleshooting failed AAA authentication attempts due to barebone information, it’s better to just look in the live logs of the AAA server if you are able to.
The tool doesn’t seem to be consistent with the information being translated, in some of the cases I was able to a translation of which IP-address was assigned to the client on a successful login, but as you can see above it never happened while I was grabbing these screenshots.
Debugging IPSec VPN’s.
As promised I mentioned we were going to go over some debug output from 2 Cisco ISRs establishing an IPSec VPN. Now I’m not going to go over every line in the debug but I’ll touch on some of the things to look out for. Now, from the beginning.
From the first line you can see ISAKMP is enabled and it starts looking for it’s peer (172.17.1.1 in this case), the router realizes it needs to use main mode and it locates the PSK for this particular peer, so right off the bat we know the peer we are establish a IPSec VPN with, along with what PSK/Keyring we are going to be using. Next we see some mention of NAT-T and RFC 3947, this is essential so both devices know if there is any NAT”ing done in between the two devices and if so where it is being done. (If you want a bit more information on that I’d say give RFC3947 a glance over, it tells you why this is done) Next you will see the line New State = IKE_I_MM1 meaning the first packet in the IKE Phase I process has been sent out, following by the router so nicely telling us (with line beginning Main Mode exchange). Next you see the ISAKMP state change to MMO_NO_STATE, this is because we have sent out a packet but we have not received a response yet, so we are unable to continue along with the process. Then in the second to last line we see Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH meaning we received a response from the peer (the second packet in the process).

Now that we received the second packet (which contains the remote device ISAKMP polices) this router will compare the remote peers ISAKMP policies to it’s own, you’ll notice right after it says the atts are acceptable, so our policies match! You’ll also see the last 3 lines mention the lifetime: 86400 this is default ISAKMP lifetime in seconds you will want these to match on both sides of the tunnel, it’s not something to be really concerned about when building VPN’s between two Cisco devices but I would pay attention to it when building VPNs between different vendors.
Next we see the ISAKMP state proceed to MM_SA_SETUP which is another confirmation that the ISAKMP policies match and the 2 peers are going to continue along with the process. Also notice the the progressions of Old State = IKE_I_MM2 New State = IKE_I_MM3 and Old State = IKE_I_MM3 New State = IKE_I_MM4 telling us the third and fourth packets have been exchanged, shortly after that you see the router processes the NONCE payload which is used to generate the DH secret.
Now that we have exchanged the first four packets it starts authenticating the peer using the configured method (PSK in this case), and we see this in the line Sending packet to 172.17.1.1 my_port 500 peer_port 500 (i) MM_KEY_EXCH, and the line Old State = IKE_I_MM4 New State = IKE_I_MM5 telling us the fifth packet has been sent. Right after we see that we received the response packet from the peer in line Received packet from 172.17.1.1 dport 500 sport 500 global (i) MM_KEY_EXCH, then after it processes the payload, we see the line SA authentication status: authenticated, telling us the peer successfully authenticated phase I.
The above output just verifies everything we saw and said in the previous output, it shows us we received the sixth packet (Old State = IKE_I_MM5 New State = IKE_I_MM6), and Main Mode has been complete in the following lines. Input =IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE and Old State = IKE_I_MM6 New State = IKE_P1_COMPLETE.
These next group of lines tell us that phase II quick mode is starting and ISAKMP status is QM_IDLE. Then we see the router sends the first packet in the process and receives the second packet in the quick mode process from the remote device, after that it begins to process the payloads.
Now that we received the second packet from the remote device which contained its IPSec transform-sets the router compares it to its own transform-sets. The router then accepts the transform-set, as long as it matches its own transform-set and, it does. We know this because of the line atts are acceptable and it creates IPSec SAs with the peer (in the line Creating IPSec SAs).
Now, that the IPSec SAs have been established the process is pretty much complete and the IPSec VPN (both phase I and II) is negotiated and formed. There is still some more output displayed. The first 10 of so lines tell us the SPI’s associated with these IPSec peers and the IPSec security association lifetimes, like ISAKMP lifetimes you will want the IPSec lifetimes to match as well. Now there are another dozen of so lines left but the key line in middle of that Old State = IKE_QM_R_QM2 New State = IKE_QM_PHASE2_COMPLETE is the one that tells Phase II quick mode is complete and was successful. As if forming IPSec SAs were not enough.
So there we have the typical debug output of an IPSec VPN, assuming everything is configured properly on both ends, now hopefully after going this and my post from a few weeks ago going over IKE in general you’ll have a deeper understanding of what really goes on when a routers try to form an IPSec VPN.
